
Monitored vs Unmonitored Alarm...
Recent UK crime data sho...


Our mission is to make people and places safer, smarter, and stronger every day.

Comprehensive security services protect businesses, assets, and people effectively.
Our mission is to keep your spaces efficient and welcoming for everyone who uses them.

Facilities services ensure smooth operations, maintenance, and efficiency for businesses.
Our mission is to provide intelligent solutions to protect, monitor, and secure people and properties always.

Advanced security systems safeguard properties with smart, reliable protection solutions.
Our mission is to deliver tailored solutions for every sector, enhancing and security across all environments.

Diverse sectors served with tailored solutions ensuring safety, efficiency, and growth.
We create solutions that keep you safe while helping your business thrive, grow, and succeed everywhere.

We’re all about creating solutions that keep you safe and thriving

We’re on a mission to protect people, property, and peace of mind-because everyone deserves to feel safe, secure, and supported wherever they live, work, or visit.
Find out more about our people, technology and ESG initiatives for your sector.

Advanced security systems safeguard properties with smart, reliable protection solutions.
Advanced security systems safeguard properties with smart, reliable protection solutions.

Advanced security systems safeguard properties with smart, reliable protection solutions.

Facilities services ensure smooth operations, maintenance, and efficiency for businesses.

Comprehensive security services protect businesses, assets, and people effectively.

Facilities services ensure smooth operations, maintenance, and efficiency for businesses.

Advanced security systems safeguard properties with smart, reliable protection solutions.

Facilities services ensure smooth operations, maintenance, and efficiency for businesses.

Comprehensive security services protect businesses, assets, and people effectively.

Advanced security systems safeguard properties with smart, reliable protection solutions.

Comprehensive security services protect businesses, assets, and people effectively.

Advanced security systems safeguard properties with smart, reliable protection solutions.
Dedicated to safeguarding people, property, and progress with unmatched protection and professionalism.
Projects successfully delivered nationwide
Highly trained security professionals
Long-term, satisfied client partnerships
Industries and sectors we protect
We provide security solutions to protect what matters most to you.


Every Intraguard officer undergoes rigorous vetting, SIA licensing, and continuous training. Our professionals combine discipline with expertise, ensuring clients receive reliable, trustworthy, and highly skilled protection at all times.

Our dedicated teams are on standby around the clock, ready to respond within minutes. With clear escalation protocols and direct coordination with authorities, Intraguard ensures immediate action and client reassurance.

Leveraging advanced analytics, real-time monitoring, and incident reporting, we deliver measurable security outcomes. Intraguard transforms raw data into actionable insights, ensuring safer environments and long-term peace of mind.
Learn more about our people, innovation and ESG actions.
View all Blogs & Posts
Recent UK crime data sho...

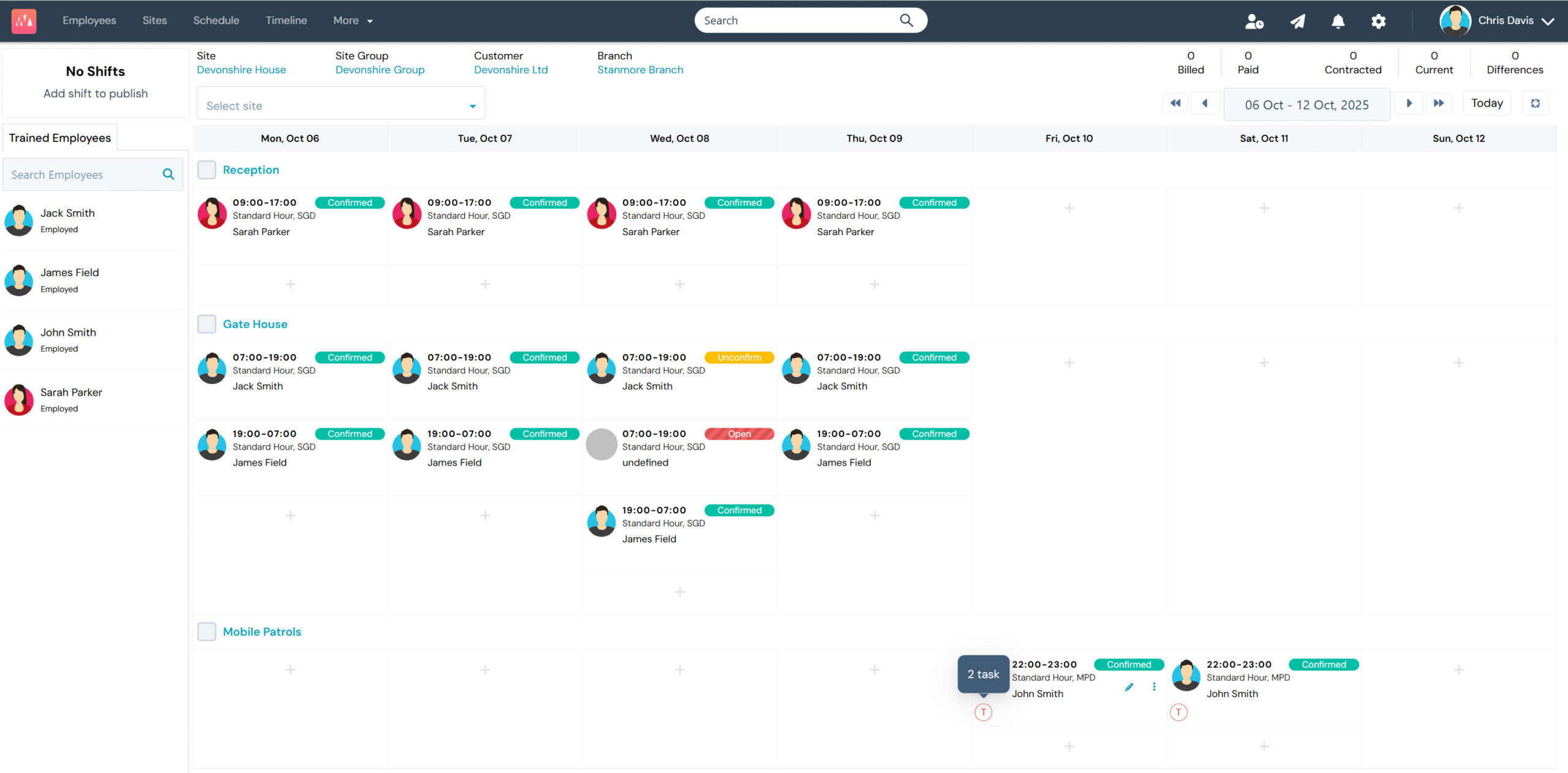
A workforce management s...


They also work faster th...


This means no matter wha...

When you’re running a business, it’s imperative that everything runs like clockwork. The environment needs to bring the best out of our employees, while visitors and customers should be instantly impressed.
Our integrated facilities management services for commercial customers help you deliver uninterrupted and hassle-free services while we keep everything in perfect working order behind the scenes.





